AWS Config allows you to monitor changes to your AWS environment and record those changes to an S3 bucket. You can also use AWS Config for remediation when something is out of compliance. Have you ever enabled RDP or another service to allow temporary access and then forgot to remove the security rule? AWS Config is a great tool for monitoring this type of activity. In this post I will walk you through creating a Config rule that monitors public access to RDP.
AWS Config setup
Choose your region then open Config under Management & Governance
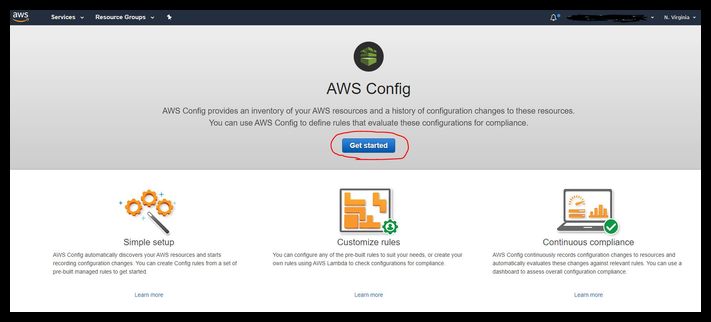
When you open Config for the first time you'll see this screen
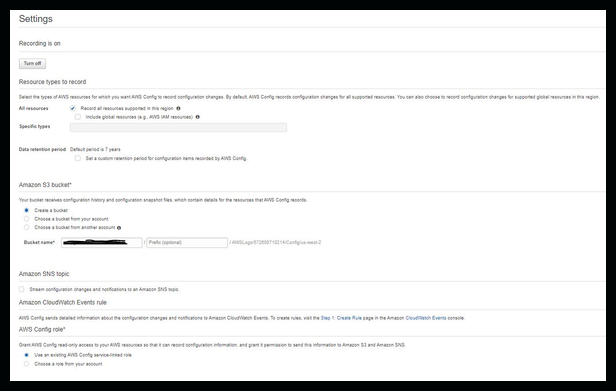
The settings page opens when you setup your Config rule. You can change these settings or leave the defaults.
Click on image to see larger version
The next step is to pick one of the preconfigured rules or create your own
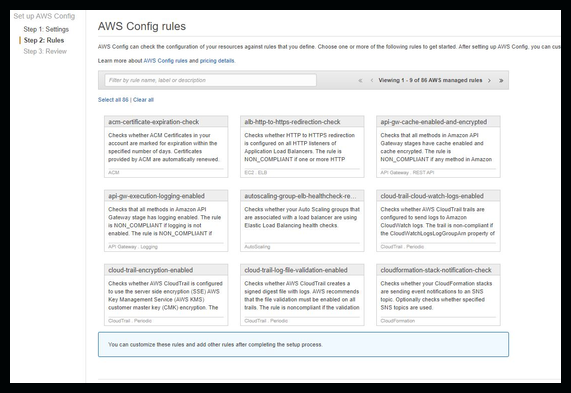
We'll go with one of the preconfigured rules. Search for restricted-common-ports
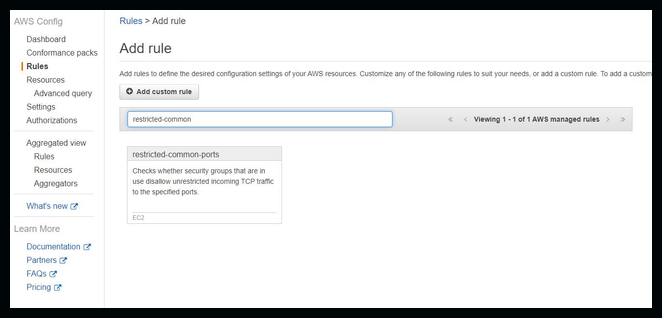
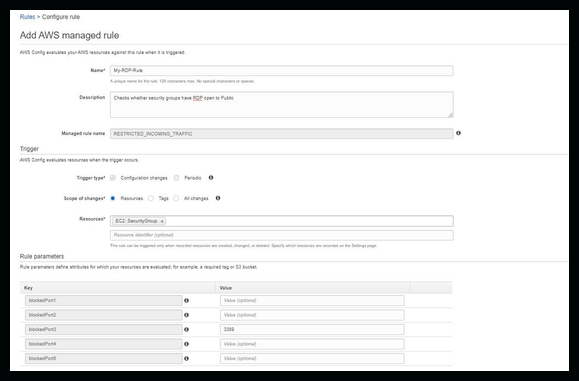
Once you choose the restricted-common-ports rule you'll be giving the option to change settings within that rule as listed below. In this demo I'm only changing a few fields.
I also removed some of the other ports that are monitored by default.
Click on image to see larger version
Here is the bottom half of the screen. Remediation has a dropdown which allows for many tasks.
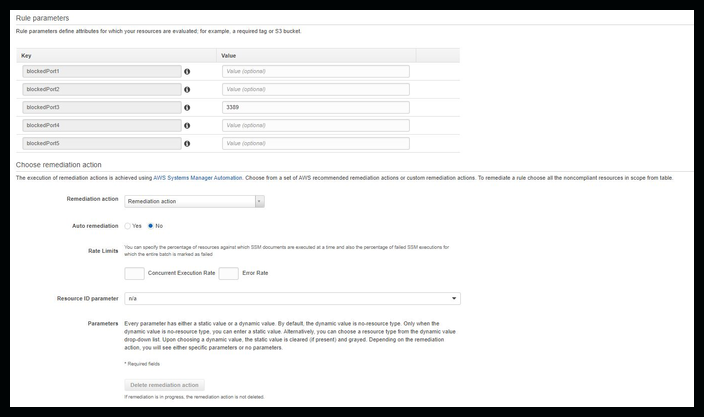
Click on image to see larger version
After you save the rule you can wait for it to evaluate or manually force it by hitting the re-evaluate button.
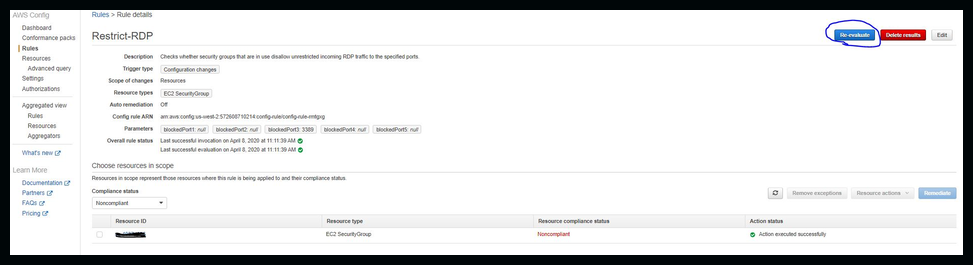
Click on image to see larger version
Once your rule is evaluated you can go back to the Config Dashboard and see the status and open the resource from here to make necessary changes to get back into compliance.
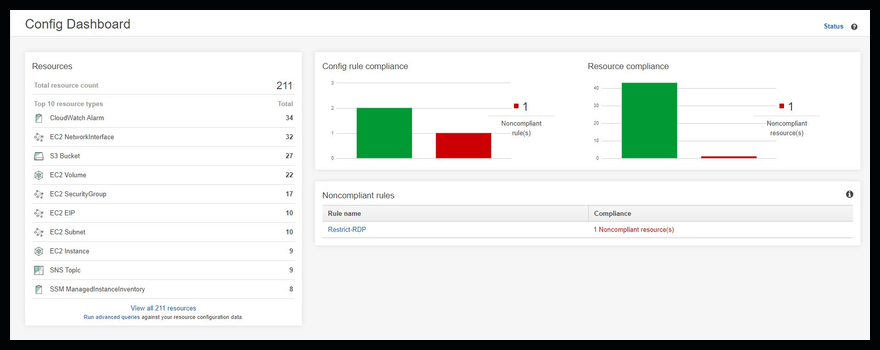
Click on image to see larger version
That’s it. You just created an AWS Config rule that will evaluate whether RDP has been opened on any security group in that region. To enable this rule in other regions you’ll have to follow the same steps for each region.













